Table of Contents
This chapter describes how to configure your LEAF system(s) to build Virtual Private Networks (VPN) with Openswan.
The setup described here assumes you are using openswan 2.4.x with
KLIPS (virtual interface support) Furthermore the setup used for this
chapter is based on LEAF systems connected to the internet via static
IP's. If you don't have a fixed ip, use the ezipupd.lrp
package and a dynamic DNS service like www.dyndns.org.
In the following sections we describe a setup for connecting subnets behind 2 LEAF systems. For the example, these systems are called west and east, and both have a DNS name like west.dyndns.org and east.dyndns.org. Please remember that these names are only examples, use real ones instead!
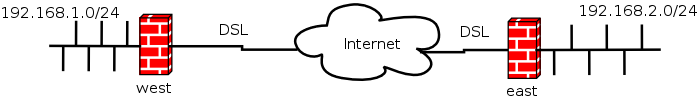 Example
Setup
Example
Setup
Openswan implements the IPSec Internet Standard for Linux. It is not the only solution but it is based on the oldest implementation of IPSec for Linux called FreeSwan. The FreeSwan project ended some years ago and their code base was used to create openswan. The feature list includes X.509 Certificates, support for nat-t and aggressive mode. It might be a good idea to take a look at the openswan Homepage for a brief description of the features of this software.